Top five e-threats – April 2010
May 2010
IT in Manufacturing
April’s top brings forward two newcomers: a fake AV and a Trojan.Keygen!
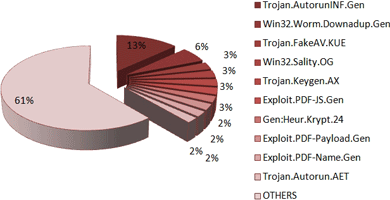
April is the third month in a row in which Trojan.AutorunInf.Gen is the top e-threat with 13,21% of the total amount of the global malware. This reveals that removable devices are used on a large scale and their owners are not that aware – still – of the damage waiting for them in the tiny gadgets.
Win32.Worm.Downadup.Gen (Kido or Conficker) is to be found once again shadowing the top Trojan.AutorunInf.Gen with 5,77%. It is the result of a successful exploitation of a Microsoft Windows vulnerability and unfortunately people are hesitant towards updating their operating systems and antivirus solution so as to easily get rid of this obstinate worm.
Ranking third is a newcomer - Trojan.FakeAV.KUE - with a percentage of 2,72 of the total amount of infections. It is not much of a surprise here, since this past week has been mostly about rogue AV. This detection covers JavaScript code that is used to trigger fake alerts on websites connected to the placement of rogue antivirus software. These scripts are hosted on malicious sites and innocent
victim-pages that have been infected.
Win32.Sality.OG is positioned fourth (2,72%) in April’s malware chart, exactly as last month - again as the sole representative of the file infector software. Shielded by a polymorphic packer, the Sality family is extremely difficult to detect and annihilate. In addition to that, the rootkit component of the virus tries to disable various antivirus applications installed on the infected system.
The second new comer of this month’s is Trojan.Keygen.AX – April’s top number five, which intercepts and blocks threats related to cracks, patches and keygens. Generating keys and patches for various applications is a common practice for commercial software on the Internet, P2P platforms, and instant messenger, download sites, social networking environments. It may be popular, but it is also illegal and risky. So, play fair and safe!
Overview of April’s malware distribution chart:
BitDefender’s April 2009 top 10 e-threat list includes:
1. Trojan.AutorunINF.Gen 13,21
2. Win32.Worm.Downadup.Gen 5,77
3. Trojan.FakeAV.KUE 2,72
4. Win32.Sality.OG 2,72
5. Trojan.Keygen.AX 2,66
6. Exploit.PDF-JS.Gen 2,57
7. Gen:Heur.Krypt.24 2,38
8. Exploit.PDF-Payload.Gen 2,34
9. Exploit.PDF-Name.Gen 2,12
10. Trojan.Autorun.AET 2,05
Others 61,40
For more information contact Alina Anton, senior PR and marketing coordinator, EMEA & APAC business unit, BitDefender, +40 212 063 470, [email protected], www.bitdefender.com
Further reading:
Why choose between Capex and Opex if you can Totex?
Schneider Electric South Africa
IT in Manufacturing
In a sector marked by cyclical demand, high capital intensity, and increasing regulatory and sustainability pressures, mining, minerals and metals (MMM) companies are re-evaluating how they approach procurement and investment.
Read more...
AI and the smart factory
Schneider Electric South Africa
IT in Manufacturing
Imagine walking into a factory where machines can think ahead, predict problems before they happen and automatically make adjustments to realise peak performance. This isn’t science fiction, it’s happening right now as AI continues to transform how we run industrial operations.
Read more...
Why your supply chain should be a competitive advantage
Schneider Electric South Africa
IT in Manufacturing
The last five years have placed unprecedented strain on global supply chains. Leading companies are turning the challenge into an opportunity to transform their supply chains into a competitive advantage.
Read more...
Why AI will never truly understand machines
Wearcheck
IT in Manufacturing
Cutting-edge technology and solutions powered by AI are embraced by specialist condition monitoring company, WearCheck, where the extreme accuracy of data used to assess and diagnose machine health is paramount.
Read more...
Buildings and microgrids for a greener future
Schneider Electric South Africa
IT in Manufacturing
Buildings are no longer passive consumers of power. Structures of almost every size are evolving into dynamic energy ecosystems capable of generating, storing and distributing their own electricity. Forming part of this exciting transformation are microgrids.
Read more...
Traditional data centres are not fit for purpose
IT in Manufacturing
Traditional data centre designs are falling short, with nearly half of IT leaders admitting their current infrastructure does not support energy or carbon-reduction goals. New research commissioned by Lenovo reveals that data centre design must evolve to future-proof businesses.
Read more...
AI agents for digital environment management in SA
IT in Manufacturing
The conversation about artificial intelligence in South Africa has shifted rapidly over the past year. Among the technologies changing the pace of business are AI agents - autonomous, task-driven systems designed to operate with limited human input.
Read more...
AI-powered maintenance in future-ready data centres
Schneider Electric South Africa
IT in Manufacturing
The data centre marketplace often still relies on outdated maintenance methods to manage mission-critical equipment. Condition-Based Maintenance (CBM) is powered by AI and is fast becoming a necessity in ensuring both competitiveness and resilience.
Read more...
Powering up data centre mega development
IT in Manufacturing
Parker Hannifin has secured a major contract to supply key equipment for nearly 30 aeroderivative gas turbines powering a new hyperscale data centre in Texas.
Read more...
Building resilient supply chains through smarter e-procurement
RS South Africa
IT in Manufacturing
In a time of constant disruption, from supply chain uncertainty to rising operational costs, businesses that embrace digital procurement are better positioned to stay competitive and resilient.
Read more...