BitDefender spotlights piracy as the weak link of on-line safety
1 April 2011
IT in Manufacturing
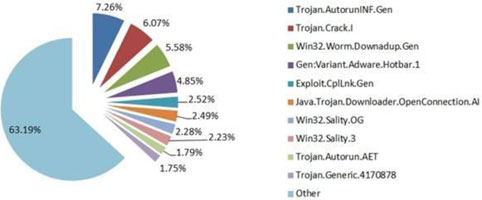
The malware charts for the first quarter of the year sees malware related to software piracy ranking high, as outlined by the BitDefender antimalware intelligence data. The Autorun function of removable devices still remains the number one vulnerability exploited by cybercriminals; and illegal advertising holds on to an ‘honourable’ and steady fourth place in the Q1 2011 e-threat top.
Malware distribution for January - March 2011:
On the highest position in the e-threat distribution chart at the end of Q1, 2011 BitDefender spots Trojan.AutorunINF.Gen that accounts for a percentage of 7,26 from the total amount of detections worldwide. This makes the autorun function of the removable devices vulnerable to malware attacks of all kinds. The constant presence of the worm in BitDefender’s top 5 malware reveals that users are still reluctant to installing security updates from the operating system vendor.
Trojan.Crack.I accounting for a percentage of 6,07 points ranks second after only a few months of existence. It should be mentioned that this application generates unauthorised registration keys in order to defeat the commercial protection of shareware software products. It may also try to collect details about further applications that run on the compromised computer (name, version, registration keys etc,) and send them to a remote attacker who would subsequently sell these licenses as OEM Software.
Win32.Worm.Downadup.Gen ranks third with 5,58% from the total number of infections registered worldwide this first quarter of 2011. There are countries like the United Kingdom where this malware saw a significant drop in detection, but there are other regions where it still dominates the malware charts (like Romania and Spain). This worm’s agenda is well-known by now: amongst others, it prevents users from accessing both Windows Update and security vendors’ web pages, while also downloading rogue AVs on the compromised computers.
Gen:Variant.Adware.Hotbar.1 accounts for 4,85% of the total amount of malware which places it fourth in this year’s quarterly malware distribution chart. Gen:Variant.Adware.Hotbar.1 forces pop-up messages on users’ PC screens, while also initiating new browser windows usually located on the right side of the desktop. This family of malware is also capable of browser hijacking, which means that most of the search queries will be routed to various ad campaigns which boost the attacker’s advertising revenue. This adware tool can be used to gather data on the surfers’ habits in order to serve targeted ads or shopping suggestions.
The fifth place in this quarterly malware top goes to Exploit.CplLnk.Gen - a detection specific to lnk files (shortcut files) that makes use of a vulnerability in the Windows OSes to execute arbitrary code. This exploit has seen a significant boost these past few weeks and it is expected to spread even further. It is also one of the four zero-day exploits that have been intensively used by the Stuxnet worm to compromise local security.
Further reading:
Sustainable energy management
Siemens South Africa
IT in Manufacturing
Utilising its innovative ONE approach technology, Siemens provides complete transparency on resource consumption and offers data-driven optimisation recommendations for sustainable energy management.
Read more...
Paving the way for a carbon-neutral future in South Africa
IT in Manufacturing
At ABB Electrification, we believe the infrastructure of the future must do more than support daily operations, it must anticipate them. We are committed to building intelligent systems that connect and optimise infrastructure across sectors.
Read more...
Africa’s hidden AI advantage
IT in Manufacturing
Through my work implementing AI systems across three continents, I’ve become convinced that Africa’s unique context demands urgent AI adoption. Successful implementation requires local expertise to understand resource constraints as design parameters to create the innovations that make technology truly work under real-world conditions.
Read more...
Siemens Xcelerator empowers space-tech pioneer, Skyroot Aerospace
Siemens South Africa
IT in Manufacturing
Siemens Digital Industries Software has announced that Skyroot Aerospace, a leading private space launch service company in India, has adopted Polarion software from the Siemens Xcelerator portfolio to digitally transform its software development processes and enhance efficiency as it aims to accelerate access to space for its customers worldwide.
Read more...
Water is running out, is your ESG strategy ready?
IT in Manufacturing
Water is one of the most critical yet undervalued resources in modern business. Water stewardship asks businesses to understand their water footprint across the entire value chain and to engage with others who share the same water resources.
Read more...
Cybersecurity in 2025: Six trends to watch
Rockwell Automation
IT in Manufacturing
Rockwell Automation’s 10th State of Smart Manufacturing report finds that cybersecurity risks are a major, ever-present obstacle, and are now the third-largest impediment to growth in the next 12 months.
Read more...
The state of the smart buildings market in 2025
IT in Manufacturing
Smart buildings are entering a transformative phase, driven by sustainability goals, technological innovation and evolving user expectations. According to ABI Research’s latest whitepaper, the sector is undergoing a strategic overhaul across key areas like retrofitting, energy efficiency, data-driven operations and smart campus development.
Read more...
Digital twin for Bavaria’s National Theatre
Siemens South Africa
IT in Manufacturing
Siemens and the Bavarian State Opera are digitalising the acoustics in Bavaria’s National Theatre in Munich, Germany. The result is a digital twin that simulates sound effects, orchestral setups and venue configurations in a realistic 3D acoustic model so that musicians, the director and conductors can assess a concert hall’s acoustics even before the first rehearsal.
Read more...
How AI can help solve South Africa’s water crisis
IT in Manufacturing
Climate change, ageing infrastructure, pollution and unequal access are putting intense pressure on the country’s water systems. A powerful question arises: “Can artificial intelligence help us change course?”
Read more...
Backup has evolved, but has your strategy?
IT in Manufacturing
With cyber threats rising and compliance standards tightening, South African organisations are under growing pressure to revisit their data protection strategies. The era of treating backups as a box-ticking exercise is over.
Read more...