Facebook Hacker – a dangerous tool
August 2010
IT in Manufacturing
A do-it-yourself kit that will enable ill-intentioned people to steal usernames and passwords to all sorts of accounts.
Phishing is known to be the weapon of choice for all cybercriminals that are after login credentials. However, a new attack tool – Facebook Hacker - has drawn attention to the criminals in need of passwords and usernames that are not theirs. This do-it-yourself kit helps the wrongdoer steal login credentials from whoever was targeted without the user even having to type in any of these details.
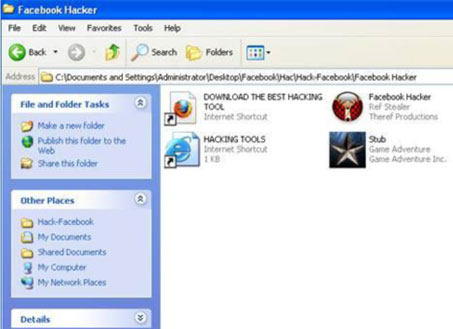
Figure 1. The extracted archive of the Facebook Hacker
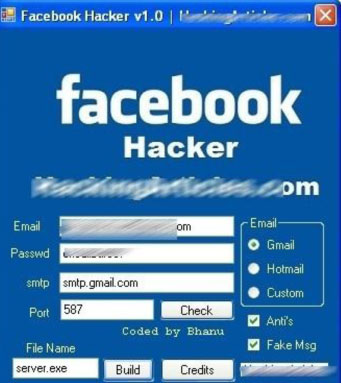
The kit is intuitive, thus extremely easy to configure, just like any do-it yourself hack tool designed with the 'skiddie' in mind. There are only two fields that need filling in: a disposable e-mail and a password that will eventually constitute the location where the stolen information is to be delivered to.
Figure 2. Configuration panel
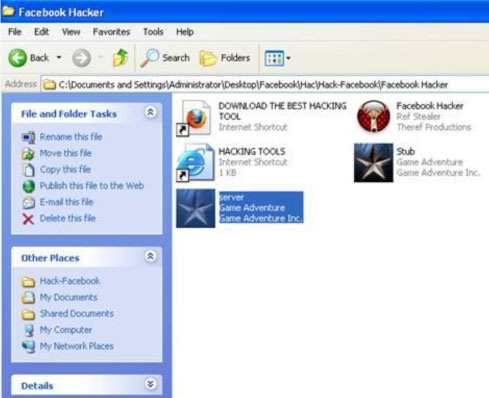
After clicking the 'build' button, a server.exe file is created and deposited into the facebook Hacker folder along with the initial files. This server.exe file is to be sent to the intended victims.
Figure 3. The server file to be sent to the victims is ready for distribution
Once run, the malicious tool will snatch the victim’s Facebook account credentials, along with all the usernames and passwords that we carelessly ask the browser to remember for us. Facebook Hacker also targets the Internet browser and Instant Messaging clients to pick up the user’s 'remembered' identification data.
In order to successfully collect passwords, the malicious binary includes applications able to squeeze data out of the most popular browsers on the market, as well as of almost all instant messaging clients available. To add insult to injury, the application also enumerates all dialup/VPN entries on the computer and displays their logon details: user name, password, and domain.
To avoid detection, the facebook Hacker will also look for all the processes related to a security suite and kill them upon detection. It is important to mention that it is accessorised with a hard-coded list of processes associated with AV solutions that are to be checked and stopped, if found.
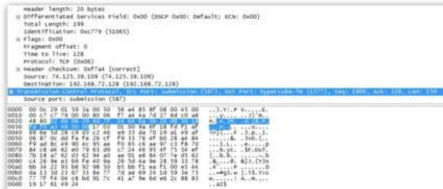
Last but not at all the least, the piece of malware looks for network monitoring applications and terminates them. This is a safety measure that will prevent curious users from seeing their passwords leave the system.
Figure 4. TCP dump of the information sent by the application. Since the SMTP server uses TLS encryption, sniffed traffic will not reveal much of what is going on
As can be seen, the author took a lot of time to think of various elements that could interfere with the smooth operation of this tool and to eliminate them one by one.
All product and company names mentioned herein are for identification purposes only and are the property and may be trademarks of their respective owners.
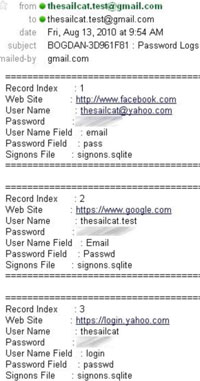
Figure 5. The stolen credentials of our test accounts are e-mailed to the specified address
BitDefender identifies this threat as Trojan.Generic.3576478. In order to stay safe, please ensure that you are running a frequently updated antivirus utility. Also, remember not to run files you may receive as attachments or via IM, or at least, to scan them beforehand.
Further reading:
Why choose between Capex and Opex if you can Totex?
Schneider Electric South Africa
IT in Manufacturing
In a sector marked by cyclical demand, high capital intensity, and increasing regulatory and sustainability pressures, mining, minerals and metals (MMM) companies are re-evaluating how they approach procurement and investment.
Read more...
AI and the smart factory
Schneider Electric South Africa
IT in Manufacturing
Imagine walking into a factory where machines can think ahead, predict problems before they happen and automatically make adjustments to realise peak performance. This isn’t science fiction, it’s happening right now as AI continues to transform how we run industrial operations.
Read more...
Why your supply chain should be a competitive advantage
Schneider Electric South Africa
IT in Manufacturing
The last five years have placed unprecedented strain on global supply chains. Leading companies are turning the challenge into an opportunity to transform their supply chains into a competitive advantage.
Read more...
Why AI will never truly understand machines
Wearcheck
IT in Manufacturing
Cutting-edge technology and solutions powered by AI are embraced by specialist condition monitoring company, WearCheck, where the extreme accuracy of data used to assess and diagnose machine health is paramount.
Read more...
Buildings and microgrids for a greener future
Schneider Electric South Africa
IT in Manufacturing
Buildings are no longer passive consumers of power. Structures of almost every size are evolving into dynamic energy ecosystems capable of generating, storing and distributing their own electricity. Forming part of this exciting transformation are microgrids.
Read more...
Traditional data centres are not fit for purpose
IT in Manufacturing
Traditional data centre designs are falling short, with nearly half of IT leaders admitting their current infrastructure does not support energy or carbon-reduction goals. New research commissioned by Lenovo reveals that data centre design must evolve to future-proof businesses.
Read more...
AI agents for digital environment management in SA
IT in Manufacturing
The conversation about artificial intelligence in South Africa has shifted rapidly over the past year. Among the technologies changing the pace of business are AI agents - autonomous, task-driven systems designed to operate with limited human input.
Read more...
AI-powered maintenance in future-ready data centres
Schneider Electric South Africa
IT in Manufacturing
The data centre marketplace often still relies on outdated maintenance methods to manage mission-critical equipment. Condition-Based Maintenance (CBM) is powered by AI and is fast becoming a necessity in ensuring both competitiveness and resilience.
Read more...
Powering up data centre mega development
IT in Manufacturing
Parker Hannifin has secured a major contract to supply key equipment for nearly 30 aeroderivative gas turbines powering a new hyperscale data centre in Texas.
Read more...
Building resilient supply chains through smarter e-procurement
RS South Africa
IT in Manufacturing
In a time of constant disruption, from supply chain uncertainty to rising operational costs, businesses that embrace digital procurement are better positioned to stay competitive and resilient.
Read more...