

In this white paper, we first outline three key distinguishing characteristics of ICS networks and the unique network security requirements compared to IT networks.
Abstract
Next, we summarise the best practices of ICS cybersecurity, which uses the ‘defence-in-depth’ design recommended by the American National Standards Institute (ANSI) and the International Society of Automation (ISA). Then, we identify key hurdles that must be overcome to achieve these best practices. Finally, we present solutions that forward thinking ICS operators have deployed to realise robust cybersecurity on their ICS networks, including an ICS cybersecurity case study from an oil and gas pipeline monitoring application.
Industrial control system (ICS) networks may have characteristics in common with IT networks and use similar equipment, but the two types of network differ in three important ways. Understanding these differences and the key characteristics of an ICS is the first step to building a robust network security solution.
Fact 1: Critical devices and scada systems on ICS networks require more protection than can be provided by an IT firewall.
Enterprise IT networks and ICS networks operate in very different worlds. Whereas an IT network is concerned primarily with PCs, servers, smart-phones, and even printers, an ICS network’s core responsibility is the very physical world of automation devices such as PLCs, I/O devices, analysers, and scada systems. An important consideration is that the IT firewall rules that restrict access to TCP/IP and TCP/UDP ports do not apply to industrial protocols, which are not Ethernet-based. In fact, one of the main requirements of ICS network security is understanding the data type used by the industrial devices on the network, since this knowledge is needed to prevent unauthorised control packets from crippling the operation. You should also keep in mind that some industrial protocols, such as Modbus TCP, do not support security mechanisms, which makes Modbus devices susceptible to both intentional attacks and unintentional abnormal operation.
Fact 2: ICS networks place greater emphasis on system availability.
Security priorities for IT networks are expressed as CIA: confidentiality, integrity, and availability, with the greatest emphasis placed on confidentiality. In contrast, security priorities for ICS networks are expressed as AIC: availability, integrity, and confidentiality, with the greatest emphasis placed on availability. This is because ICS networks are used to manage and synchronise physical operations, such as production or assembly lines in a factory, and delays in transmitting data to mission-critical controllers can result in financial losses, or even endanger human life.
Fact 3: ICS networks face a different set of threats.
Both IT and ICS networks must defend against intentional hacker attacks as well as worms or viruses introduced unintentionally by authorised users. However, ICS networks have the added complication that in addition to managing security issues from personnel, they must also focus on the machines themselves. For example, out-of-order machines may produce unexpected broadcast storms of Ethernet packets that disrupt the operation of other machines. In addition, both industrial PCs infected with viruses and out-of-order devices can easily compromise the performance of an ICS network and in this way affect availability.
Deploying ICS network security: challenges and criteria
Deploying ICS network security involves a trade-off between cost and risk management. For example, critical infrastructures such as national utilities naturally demand higher levels of protection, leading to higher costs. Attacks from malicious malware are easier and less costly to defeat, whereas it is more difficult to protect against human hackers. The most common counter measures for protecting ICS networks are to increase vigilance and introduce mechanisms that complicate the attack process so much as to dissuade hackers from even trying. These measures are at the heart of the so-called defence-in-depth strategy recommended by industry experts.
Defence-in-depth cybersecurity
Recognising the unique security challenges facing ICS networks, ANSI and the ISA have promulgated the ANSI/ISA-99 (IEC 62443) standards, which describe best practices for ICS security. Central to the ANSI/ISA-99 standard is the ‘zone and conduit’ security model, which is implemented with a defence-in-depth strategy.
In the ANSI/ISA-99 model, ICS devices are segmented into independent ‘zones’, composed of interconnected devices that work closely together to achieve a specific function. While communications within a zone are less restricted, different zones are required to communicate with each other through a single point, called a ‘conduit’, which is usually protected by a secure router or firewall. The conduits are robustly protected to allow only the specific data that is needed to coordinate the functions of the different zones. Any communications that are irrelevant to the function of a certain zone, such as http traffic to a Modbus TCP zone, will be blocked by the secure router.
Obstacles to deploying a defence-in-depth strategy
The most critical part of an ISA-99 security model is the conduit, which is protected by a secure router and must handle a number of responsibilities:
* High network performance: As the point of contact between two network zones, the secure routers must have the level of network performance needed to filter and deliver all of the traffic in a timely enough manner so that network availability is not affected.
* Deep packet inspection: As the security guardian between adjacent zones, the secure routers must be able to inspect the content of the packets of industrial protocols for abnormalities and security threats.
* Deployment complexity: The high-density deployment of secure routers needed for protected ICS networks requires more effort to maintain, both Ethernet switches (for the network infrastructure) and secure routers (for the firewall).
Let’s examine the challenges of each of these responsibilities in greater detail.
High network performance
Any device that connects between subnets can expect to see a lot of traffic. ANSI/ISA-99 conduit devices are effectively backbone devices that connect different ICS subnets. Modern ICS systems also require more and more bandwidth to support the sophisticated applications that they run, such as video. In addition, some DCS networks call for gigabit-based networks for efficient communication. In order to maintain network availability, a zone conduit must provide the service required all while acting as a firewall and filtering inappropriate data without compromising performance.
Deep packet inspection
A conventional network firewall is not sufficient for the specified communications requirements of an ICS because the conventional firewall is blind to the contents of industrial communications protocol packets (such as Modbus TCP). This is a particularly critical problem since industrial communications protocols generally have very poor security. Industrial devices simply respond to any packets they receive, including read queries, shutdown commands, firmware updates and control commands. The network conduit needs to know the contents of a packet to sort safe packets, such as read queries, from potentially unsafe packets, such as shutdown or wipe commands.
Deployment complexity
The conventional way of deploying cybersecurity on an ICS network is to add secure routers or firewall equipment that act as secure conduits, which is in addition to the existing network hardware, such as layer 2 switches. Protecting one factory site requires only one or two high performance secure routers, whereas protecting network zones could require tens of secure routers. However, cybersecurity best practice dictates that security must be implemented at the device cell level, which could involve hundreds of secure routers or firewalls to be deployed at field sites. As you can easily surmise, installing and managing such a device structure would require both high cost and a herculean effort.
Overcoming the challenges
Moxa’s new EDR series of industrial secure routers gives managers of ICS networks all the tools they need to create the type of layered security that fulfils the guidelines set out in ANSI/ISA-99.
High throughput: Moxa’s EDR family of secure routers has gigabit uplinks and easily supports large amounts of network traffic. Even when inundated with traffic, the EDR secure routers deliver enough throughput to provide seamless video support.
Deep packet inspection: In addition to firewall, VPN, and NAT security functionality, the EDR-810 also supports PacketGuard for deep packet inspection of Modbus TCP packets. Modbus TCP is a commonly used industrial communications protocol, but it is not secure. With PacketGuard, the EDR-810 can scrutinise the contents of Modbus TCP packets to identify potentially damaging commands and thus protect Modbus devices from the commands, regardless of whether they are intentional or unintentional.
Integrated, cost-effective solution: The EDR-810 has a built-in switch and includes all the security functionality needed to establish a secure zone. The EDR-810’s 10 ports can be set to WAN mode (for communications outside the zone) or LAN mode (for communications inside the zone), with the firewall sitting between the WAN and LAN in the same box. This innovative integrated solution, which combines a secure router with switch functions in the same product, not only provides connectivity for devices but also protects them directly against external networks.
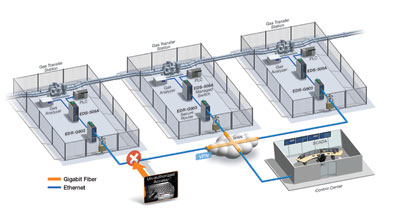
Case study: secure remote pipeline monitoring for gas transfer
Large gas pipelines use ICSs to monitor and maintain pipeline assets and gas transfer stations. In the gas pipeline system illustrated above, each gas transfer station is a secure zone, the control centre itself is also a secure zone, and secure conduits monitor the communications between each of them.
In addition to adhering to the ANSI/ISA-99 guidelines for strong packet authentication, encryption, and integrity protection, ICS security devices must also meet the following application specific requirements:
* Be able to operate in outdoor environments and temperatures ranging from -40 to 75°C.
* Gigabit, high performance fibre and copper connectivity.
* Dual WAN port redundancy for greater reliability over public networks.
By deploying Moxa’s EDR-G903, the pipeline operator was able to create truly secure zones and confidently manage the gas transfer stations from a central control centre, even when using the public Internet to connect to the individual gas transfer stations.
For more information contact RJ Connect, +27 (0)11 781 0777, [email protected], www.rjconnect.co.za
| Tel: | +27 11 781 0777 |
| Email: | [email protected] |
| www: | www.rjconnect.co.za |
| Articles: | More information and articles about RJ Connect |

© Technews Publishing (Pty) Ltd | All Rights Reserved