

What comes to mind when you hear the term ‘mission-critical infrastructure’? Depending on your experience and background, you might think of oil and gas production fields, railway station monitoring systems, power generation facilities, or highway traffic systems, to name a few. The term mission-critical should not be taken lightly since it is used to describe networks that, once they experience instability or transmission problems, could result in serious damage to equipment and facilities, or even injuries or loss of life. In recent years, video surveillance systems have played an increasingly important role in ensuring the reliability and safety of mission-critical infrastructures around the world.
Video surveillance is now standard for industrial mission-critical infrastructure
Video surveillance systems use images to allow security personnel to monitor an entire facility, or even a collection of facilities, from a central location, 24 hours a day, seven days a week, instead of hiring a large contingent of security guards to man a large number of guard stations. Surveillance systems are certainly not new, but in recent years there has been a big change in how they are implemented. A basic system might simply save all of the images onto a hard drive for future analysis when the need arises. More advanced systems, however, use intelligent cameras that support extremely sophisticated features, including the ability to recognise scene changes in critical areas (e.g., if someone leaves a backpack unattended in an airport), or identify specific types of objects. It goes without saying that a video surveillance system is already a must-have standard system for any type of mission-critical facility, both for monitoring events in real time, and for providing a library of images that will be available for future analysis.
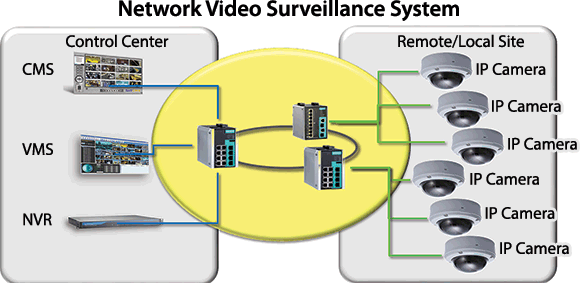
Challenges of IP-based video surveillance network design
Commercial-grade video surveillance systems are used in almost every public facility, including supermarkets, offices, and schools. But when it comes to installing a video surveillance system in a mission-critical industrial application, you need to pay special attention to the following issues:
Data transmission vs. video transmission
Transmitting video streams presents unique challenges that you may not need to consider with basic data transmissions. At the IP packet level, data and video use the same TCP/IP technology to ensure large scale, fast data transmission. But at the application level, video surveillance normally involves establishing and managing network access between multiple devices. For example, an NVR (Network Video Recorder) and a VMS (Video Management System) operating in different control rooms may want to save or show the same video stream at the same time, while a CMS (central management system) may want to display images from the same video stream on a large LCD screen. For this kind of scenario, the IP camera would usually need to send the video streams separately. For the particular case shown below, the IP camera would be required to send three video streams over the Internet.
As the number of cameras increases, the need to transmit so many video streams over the same network will occupy a huge amount of the backbone network’s bandwidth. In order to reduce the amount of bandwidth used by all of these video streams, we normally configure video streams as ‘multicast’ type. Multicast means that each IP camera only needs to send one video stream at a time, and uses Ethernet switches to reproduce and forward the same video stream to multiple receivers automatically. The following figures illustrate the difference in bandwidth requirements between unicast and multicast configurations. As you can see, using a multicast configuration can save an impressive amount of bandwidth for the entire network.

Lack of redundancy for data transmission
Most CCTV surveillance networks use a ‘star’ or ‘daisy-chain’ topology to connect and expand the number of IP cameras connected to the network. However, star topologies are not designed to recover from single points of failure. If only one network cable gets disconnected, or one network device crashes, that single point of failure could result in the disruption of a huge number of video streams. Some designers might recommend using ‘trunking’ technology to aggregate multiple Ethernet ports and cables into one transmission path. In this case, if one cable is disconnected, video data will continue to be transmitted through other ports and cables. However, this design cannot prevent interruptions to data transmission due to single node failures, as would be the case if an Ethernet switch stopped working due to a power outage in the field.
Network management efficiency
As your network gets bigger, you will probably want to use network management software to monitor and manage the status of your network and network equipment. Experience has shown that if you have more than 50 Ethernet switches on a single (or extended) network, you should consider using an NMS (network management software), since you can save a lot of time on network management tasks. However, there are three features you should consider when you choose an NMS for a video surveillance network:
Real-time monitoring: How fast can the NMS receive and then display alarms from large numbers of network devices?
Visualisation: When network alerts appear on your screen, how quickly can you locate the root cause?
Integration: Intelligent systems rely on close system integration and message exchange to ensure that your NMS can determine if end devices (IP cameras, for example) are alive or not, and provide meaningful information to higher level central management systems in the control room.
Fast Ring Network Recovery
As we mentioned above, star and tree topologies are prone to single point of failure events, which occur when only one cable or network device fails. For industrial networks, ‘rings’ and ‘redundancy protocols’ are commonly used.
The Ethernet switches are configured to use RSTP (Rapid Spanning Tree Protocol). RSTP identifies a certain number of network connections as redundant, and then blocks network transmissions through those connections to avoid looping. If one of the active network cables or switches fails, RSTP activates one of the blocked connections to ensure that all of the devices connected to the network can continue to transmit data to the required locations. However, the typical recovery time for RSTP is 2 to 5 seconds. What this means is that you could lose 60 to 150 frames (assuming 30 frames per seconds) of CCTV surveillance images. However, some industrial network device manufacturers have developed proprietary ring recovery protocols that support recovery times between 20 and 50 ms, which is a much more acceptable recovery time for mission-critical CCT surveillance networks.
Moxa’s V-ON technology keeps video streams streaming
Let’s take a look at some actual test data to see just how important it is to optimise your network for video streaming. The data compares recovery times between the standard RSTP redundancy protocol, and Moxa’s V-ON (Video-Always-On) redundancy protocol, which is optimised for video stream transmissions.
Two surveillance networks used for the test were set up in the following way:
• 16 HD IP cameras were connected to each network.
• Multicast transmission was used to transmit video streams to two NVRs.
• Redundancy protocol: Network 1 traditional ring network with RSTP redundancy protocol. Network 2 with redundancy protocol optimised for video streams
• SPIRENT SPT-9000A Ethernet package measuring equipment was used to measure video stream recovery times.
• Two scenarios were simulated: Scenario A media failure due to a disconnected cable. Scenario B node failure due to loss of power to one Ethernet switch.
Video stream recovery times after media failure and node failure, with and without optimisation are shown in the table below.

From the data shown in the table, it should be obvious that RSTP is not designed for multicast video stream redundancy. Compared with the traditional RSTP protocol, when using the optimised protocol, recovery took a fraction of the time for all of the cases tested, which shows that Moxa’s V-ON technology can optimise your network for video streams, therefore making your network suitable for mission-critical IP surveillance applications.
| Tel: | +27 11 781 0777 |
| Email: | [email protected] |
| www: | www.rjconnect.co.za |
| Articles: | More information and articles about RJ Connect |

© Technews Publishing (Pty) Ltd | All Rights Reserved