

Any number of adverse conditions can occur per process or sub-process over the duration of a shift. Some of these adverse conditions can be of a critical nature as it may pose safety risks or may result in loss of production, substandard yield or quality deviations. Other adverse conditions may be less critical, as processes tend to drift in terms of variables and set-points over time. When the process has drifted to such a degree that it becomes a critical condition, only then is action normally taken. Process drift also results in the process moving from an ideal state to a suboptimum state with the resulting negative financial effects. These adverse conditions are normally neglected as operators and managers may not even be aware that the process has moved out of the ideal state as it is not a critical event as yet.
One of the things that ‘Best in Class’ companies do better than ‘Laggards’ is to implement standards to react to adverse events. These standards can be in the form of standard operating procedures or they can be automated within systems such as MES or MOM and may include escalation and workflow. These standards to be followed in reaction to adverse events ensure that operators and managers take consistent actions for the same adverse condition. They may be biased as they may be based on opinions or unscientific experience, but they do ensure consistent action. The standards also shorten the time between the adverse event information being available and the action, as the operator or manager do not have to absorb the information, create a mental model and plan a strategy or approach before taking action. They can take action immediately.
Standardising actions for adverse events thus add a lot of value to the business, not only because it ensures the consistency of the decisions and actions, but more importantly because it reduces time between the adverse event and the action taken to rectify or counter the event. An adverse event can also be classified as an adverse plant state. In other words, a state of the plant that is sub-optimal and does not produce the right quality, at the right yield and at the lowest cost.
Adverse condition management using time-in-state metrics (TISM)
The most common standards for adverse events are defined around safety-critical events, such as plant start-up, shut-down or emergency stops. A lot of time and effort is expended in ensuring that plants or processes shut down safely, from the design phase to having their own, redundant Safety Instrumentation System parallel to the normal automation system.
From a safety perspective, this is well and good, but there remains a gap in the definition of standards for adverse conditions such as quality deterioration, low throughput or low yield. Typically actions to these adverse conditions are not defined as there are almost as many possible actions as there are variables in the plant and the correct action can only be defined once the state of the key variables in the plant is known. Because of the complexity of the relationships between the different influencing variables, the resulting actions normally taken are based on biased thinking and will differ from operator to operator.
Actions to these adverse events or states as explained above can be many and varied, depending on the event and the state of the plant. Operators do not have the time to react to all process variables all the time and cannot look at all the HMIs at all times. Operators spend their time reacting to adverse conditions only when they become critical as they often do not have the tools to show them what the optimum state of the various variables actually is.
Obviously set-points and control limits are set as standards for each variable, but in the event of process disturbances and state changes in other parts of the plant or process, the control systems may not be set to the correct set-points to control the process in the optimum state. Operators may not be aware of the state-change in the process or even if they are, it may not be of such a nature as to become critical and as such no action is taken. The change in one variable is often of no big concern, at least until it starts affecting other parts of the process or plant. If the variable, however, is one of the Key Process Influencing Factors (KPIFs), then it should be of concern as it will affect the SIT Metric and as such the financial performance of the plant.
Identifying and using KPIFs
It is critical to first determine, from basic principles, the KPIFs that impact the KPI being measured (such as yield, recovery, throughput, quality etc). These KPIFs have a complex relationship with each other and a change in one will affect the others, either in a positive or negative way. Balance needs to be maintained between the different KPIFs in order to keep the process in the correct state. Operators do not always know what the KPIFs for a specific process are, and if they do, they often do not understand the complex relationships between them. Very few plants have tools to show operators these relationships and how changes to one affects the others.
Once the KPIFs for a specific process are determined, tools need to be provided to operators to visualise the KPIFs and their relation to one another. Once these tools are provided, it will become apparent to the operators how their actions influence the state of the plant. If the KPIFs are kept in balance, then the TISM will be good, if one or some start deviating or moving out of the optimum state, the TISM will be low.
Standardising actions based on TISM
Once the complex relationships between KPIFs have been identified and visualised, the process of standardising actions to react to KPIF movement can start. Without this understanding of cause and effect it is not possible to standardise actions.
The aim of all actions will thus be crystallised into a simple process of maintaining a balance between the various KPIFs for a specific KPI. For the state of each KPIF outside of the optimum area of operation, standard actions can be defined for incremental change over a period until the optimum state is reached and balance is achieved. These standard actions can also include the effect it will have on related KPIFs and whether the action will lower or increase the other variables. With these tools, the operator will be able to make more informed decisions when taking the standard action.
Figure 1 shows a simplified control chart for Yield KPIFs. The red lines indicate the optimum state. If all the KPIF bars are between the red lines, the time will count toward the TISM. In the figure, it can be seen that in this case the temperature (PT) is too high. Lowering the temperature by increasing the cooling will thus be one of the standardised actions. However, the pressure (PP) is on the low side and if the temperature is lowered, the pressure will likely reduce as well, potentially below the lower limit. The standardised action will have to make a note of this and suggest that the flow (PF) into the process be increased at the same time to ensure adequate pressure whilst lowering the temperature to the ideal state.
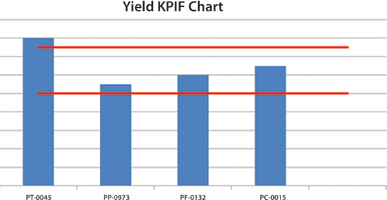
The above example is of course very simplistic (as is Figure 1), but over time, with the correct experience, actions can be standardised and refined to ensure better decisions and improved TISM results.
Not all potential actions can or should be defined and standardised. This will be a huge waste of time and energy. If the correct methodology is applied, then different KPIF states will be identified together with their probability of occurring. Only the states that have a high probability will be singled out for standardised action, where those with a low probability will not (unless they are safety critical).
For more information contact Gerhard Greeff, Bytes Systems Integration, +27 (0)82 654 0290, [email protected], www.bytes.co.za

© Technews Publishing (Pty) Ltd | All Rights Reserved