
The evolution of the process control network from individual isolated computers with proprietary operating systems and networks, to interconnect various systems and applications employing commercial-off-the-shelf technology, has led to the full integration of process control networks with business enterprise systems and other applications through various communication networks. This is known as “the plant of the future”.
The benefits of such network and system integration include:
• Increased visibility of process control network activities (work in progress, equipment status, product schedules) integrated with processing systems from the business level. This contributes to capability improvements through analysis, which drive down costs and improve productivity.
• Integrated manufacturing and production systems that have more direct access to business level information, thus enabling a more responsive enterprise.
• A common interface, resulting in a reduction of overall support costs by permitting remote access to production processes.
• Remote monitoring of the process automation system which results in reduced support costs, allowing for quick, effective problem resolution.
Plant of the future characteristics
“The plant of the future will only have two employees: a man and a dog. The man will be there to feed the dog. The dog will be there to keep the man from touching the equipment.” Warren G. Bennis.
As the quote points out, the plant of the future will have very specific characteristics which are different from that of current plants.
These include:
• Agility and flexibility: the supply chain will be fully synchronised for optimal asset utilisation.
• Synchronisation of business and plant systems.
• Autonomous operations: nearly unmanned; event prediction mitigation; intervention by exception; integrated control and safety systems.
• Be information driven: connected systems with access from anywhere to information and context.
• Asset performance management: optimised operating performance; predictive and prescriptive alerts; highly integrated operations and maintenance.
The biggest challenge facing the plant of the future will be continuous security of the information flow.
Continuous security concept
The security demands currently being made by the process control customer differ from those of classic plant security. Integration with open systems, using the latest technology devices and networks, is now a requirement. Due to fast changing technology, the possibilities are unlimited and plant security needs to cope with and address any known issues and vulnerabilities.
Just as control system technologies are constantly evolving, security risks, including attack techniques, are evolving just as fast. Attacks targeting industrial control systems have been increasing at an alarming rate. Once off deployment of security controls is insufficient to mitigate these risks. A service lifecycle solution for cybersecurity is required to ensure that the security measures and deployment are continuously enhanced, monitored and inspected.
Yokogawa’s cybersecurity lifecycle solutions
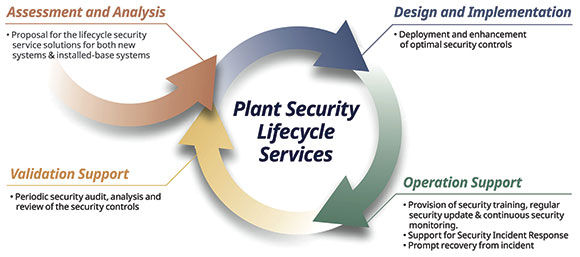
Plant security lifecycle service: Yokogawa’s cybersecurity approach has four phases, starting with an assessment of the system and ending with a validation of the security controls. This approach ensures that the design and implementation are specific not only for the industry, but for each customer’s unique environment.
Phase 2: design and Implementation – deployment and enhancement of optimal security controls.
Phase 3: operational support – provision of security training, regular security updates and continuous security monitoring. Support for security incident response and prompt recovery from incidents.
Phase 4: validation support – periodic security audit plus analysis and review of security controls.
Conclusion
For more than a decade, Yokogawa has developed and provided proprietary cybersecurity solutions and technology for its customers. During this time, the Industrial Cyber Security Group has gained invaluable experience and knowledge from various projects undertaken around the world. The company is therefore in a prime position to co-innovate with customers wanting to minimise security risks and maximise corporate value.
For more information contact Christie Cronje, Yokogawa South Africa, +27 11 831 6300, [email protected], www.yokogawa.com/za
| Tel: | +27 11 831 6300 |
| Email: | [email protected] |
| www: | www.yokogawa.com/za |
| Articles: | More information and articles about Yokogawa South Africa |

© Technews Publishing (Pty) Ltd | All Rights Reserved