

Remote access for servicing PLCs, HMI panels or other industrial equipment is becoming a must-have for most OEMs (Own Equipment Manufactures) and system integrators in order to live up to their contractual obligations. It is not just about travel budget cost reductions; more critical is the contractual obligation for response time and up time, and with the increasing complexity of industrial installations, efficient use of critical engineering resources is vital. Optimising service offerings and resources requires selection of the right solution for remote access, to ensure focus is kept on the core business.
Identify the category of remote service that covers your needs
Remote monitoring
The term remote monitoring (or remote management) typically covers collecting specific predefined information from devices, and processing them on a central server. The main purpose is to perform preventive or predictive maintenance, and if a critical problem is detected, a technician will travel on site. Note that such solutions are typically not designed to allow establishing of connections through which you can service the equipment remotely. This type of solution is very common for utility installations.
Remote service via remote desktop
Several low cost, or even free solutions, exist for providing remote desktop access to equipment inside a network. Most of the solutions require that both ends are manned, which is typically not the case for a service PC at the factory. Solutions do exist that allow secure remote access to unmanned equipment inside local networks, but these solutions are typically not cheap. Add to this the administrative task of maintaining a Windows PC (with its frequent security updates) and the potential cost of software licences for the PLC or HMI programming software packages installed on the PC, and the setup may seem less ideal .
Remote service via port forwarding
Solutions in this category are typically based on a hardware unit at the site that acts as an Internet router to the equipment. The most simple solutions are based on the router having a fixed IP address on the Internet, which 'routes' or 'port forward' incoming connections to the equipment; pretty similar to the traditional dial-up modems. This type of setup is typically seen for video surveillance. The risk of exposing access to industrial equipment directly on the Internet, using unencrypted connections, combined with the need for fixed IP addresses, essentially rules these solutions out.
Remote service via data tunnelling
This is the kind solution that would fit most remote service needs. Traditional IT solutions based on VPNs have existed for more than a decade, but in recent years, VPN solutions specifically addressing the automation industry have multiplied. Most of them are just traditional VPN solutions packaged for automation use, by offering DIN rail mounting and 24 V power feed. Some vendors have taken a step further to disguise complex IT configuration from the users and eliminate need for changing firewall settings. These solutions typically involve a central M2M server, acting as a portal for user access control and data redirection. At least one vendor, namely the Danish company Secomea, has evolved away from VPN completely, and instead uses a concept of encrypted proxy connections for solving challenges that VPN technologies by nature have difficulties to overcome.
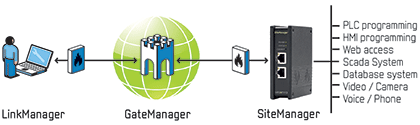
What to watch out for in relation to the above category
Ease of deployment – a vital part of overall security
Ease of installation and configuration is essential for saving time, and for enabling non IT literate personal to deploy the solution. It should not be necessary to configure firewall or routing rules, or to install third-party software that are not an integrated part of the solution. Installation and initial configuration should be possible to do by the same engineer that handles the electrical wiring, and user access control and configuration of device access should be manageable by the PLC programmer, the OEM project manager or the site administrator.
Using the customer network, and security argumentation
Typically a factory, or its machines, would run in a network isolated from the corporate office network, but typically it will only be the office network that can connect to the Internet. When using a standard VPN enabled router for accessing the machine network, you would typically connect its WAN side to the office network, and the LAN side to the machine network.
IT departments will not be happy about a third-party connection between the networks, even if you argue that the router has a built-in firewall that prevents unauthorised access between the networks. So you will have to explain precisely how the solution works and why it does not compromise security. Such information should be provided by the remote access solution vendor.
Additionally the solution must be able to establish its encrypted tunnel connection to the Internet based on ports that are commonly open. This would be 'web' ports, such as 80 (http) and 443 (https). Do not expect IT departments to open specific ports on your request.
Network conflict issues
Maybe one of the most common issues when connecting multiple users and networks together is 'network conflicts'. When connecting networks statically via routers or VPN connections, all networks must have different 'IP subnets'.
A typical issue is that two factories may use the same IP subnet. Most industrial remote access solutions solve that by dynamically establishing the connection on-demand, and close it again when done. The only limitation is that the service engineer cannot be connected to both factories simultaneously, which would typically not be necessary either.
More critical is the scenario where the engineer sits in an IP subnet that is identical to that of the factory (e.g. a user sits in subnet 192.169.0.10/24, and attempts to connect via VPN to a factory that uses the exact same subnet). For routed technologies this will simply not work. It could be solved by making alias addresses and applying NAT (network access translation), but it is not trivial.
Two-factor authentication
Typical VPNs for statically connecting office networks are based on x509 certificates that are manually exchanged between the VPN peers during the initial setup. In recent years SSL/TLS based VPN solutions have become popular, due to being 'firewall friendly' and automatic bidirectional authentication. The concern with many such implementations for industrial access is that the initial authentication is based on only a user name and a password.
Traceability and logging
Documented proof of who took access to what, and when. The purpose is not only to document if a given remote user may have been causing an issue on a machine, but also to document if a service provider is in fact fulfilling the service obligations.
Check if audit logging exists and how it can be accessed.
Dependence of third-party cloud services
As mentioned earlier, using a central M2M server is becoming essential for controlling user access and data connection redirection. Such services may be free, or be subject for maintenance fees. Investigate fees in relation to scaling the solution and make a strategy for which budget to place such cost on.
More importantly you should investigate if the M2M server is available only as a cloud service hosted by the vendor, or if you can migrate to an own M2M server. Major OEMs generally do not like to be dependent on a specific vendor’s existence for their server’s up-time and applied security measures.
For more information contact Bob Petrie, Throughput Technologies, +27 (0)11 705 2497, info@throughput.co.za, www.throughput.co.za
| Tel: | +27 11 705 2497 |
| Email: | info@throughput.co.za |
| www: | www.throughput.co.za |
| Articles: | More information and articles about Throughput Technologies |

© Technews Publishing (Pty) Ltd | All Rights Reserved