

ARC Advisory Group’s long-running research into industrial control systems (ICS) and ICS cybersecurity provides a unique vantage point for assessing the cybersecurity implications of the emerging Industrial Internet of Things (IIoT). We have closely monitored the development and adoption of ICS cybersecurity standards and best practices and believe they are having a significant impact on the security of plants and automation systems. But, IIoT is disrupting key assumptions underlying these efforts.
Recognising and addressing this situation is essential. Business managers are already redesigning processes to exploit IIoT capabilities. ARC believes that it is naïve to expect that they will wait for security to be addressed before implementing these capabilities; the cost and performance benefits are simply too large to ignore and competition will force rapid adoption.
Prudent ICS cybersecurity professionals appreciate the impact this will have on cybersecurity strategies and are looking for new guidelines. ARC believes that this should include:
• An extension of the scope of industrial cybersecurity to include systems and remote devices outside plant perimeters.
• A shift in the focus of security strategies from protecting systems to managing devices.
• Transition from cybersecurity silos to integrated IT-OT cybersecurity strategies.
• Embedding security-by-design principles throughout organisations and cyber asset supply chains.
IIoT disrupts industrial control system designs
Most organisations understand that IIoT will change their operations and create new cybersecurity challenges. Many assume that this will only involve installing additional sensors in plants and enabling external access to the associated data. However, the most popular IIoT use cases require integrating multiple technology developments with traditional control systems. These include mobility, ubiquitous connectivity, cloud computing, and smart (IoT-enabled) devices. Each of these developments represents new challenges for plant cybersecurity teams.
Mobility and ubiquitous connectivity
Enabling mobile devices within plants is already a key concern for many companies. Lack of control over mobile software and content make them as functionally insecure as public networks. Restricting use is as difficult as ever, particularly when external resources are needed to support plant issues.
This situation is only going to get worse. Business managers recognise the enormous benefits of mobility and ubiquitous connectivity and are already redesigning processes to exploit these capabilities, both within and outside plant perimeters. In the future, plant managers, supervisors and technicians will expect free access to control system information and the ability to intermix this information with information from external sources on the same device. For example, a technician troubleshooting a plant issue may require access to control devices while simultaneously using the same mobile device’s cellular capabilities to access documentation on a supplier’s website. Likewise, organisations may want this same person to have comparable access to plant assets from outside the plant perimeter, so that they can offer support at a moment’s notice.
While security concerns will be acknowledged, history suggests that they will not be enough to limit this explosion in connectivity. Plant managers will support this need for boundary less access and automation suppliers will enable ubiquitous connectivity in their products to support remote service strategies. Once connectivity is built in, system designers will freely use it to integrate remote systems, devices and applications.
From an industrial cybersecurity perspective, these developments will increase the attack surface exponentially, along with the number of threats that must be managed. This will also reduce the effectiveness of traditional strategies for managing vulnerabilities and intrusions. The proliferation of devices and users will rapidly make it impossible for organisations to track and manage software revisions and patches. Establishing security conduits and a single secure remote interface will also fall out of practice, as this will not adequately support all these needs. Cellular communications will also add a whole new set of industrial cybersecurity challenges and strain the very idea of secure perimeters.
Cloud computing
Enterprise IT groups are rapidly adopting the cloud as a platform for sharing information and managing applications across the enterprise. It enables access to resources anywhere, anytime and promotes efficiency and effectiveness through faster, more collaborative decision making. The cloud provides a way to reduce applications, simplify IT maintenance and improve security. It is also fundamental for many of the most popular IIoT uses cases, like remote maintenance.
Recent developments show that conservative ICS attitudes toward the cloud are changing as well, particularly for supervisory applications and sharing plant data with partners. Suppliers of production management, MES, and historian applications already offer cloud solutions for both private and public clouds. While they are not hardware devices, cloud-based data stores and software applications should be considered ‘virtual’ IIoT devices with associated challenges for ICS cybersecurity teams.
Like ubiquitous connectivity, the large benefits of cloud solutions have become too attractive to ignore. These benefits include reduced Capex, faster deployment, lower maintenance costs, easier upgrades and better collaboration. The proliferation of large, reliable data centres has also reduced many of the initial concerns.
The security impact of the cloud differs from that of ubiquitous connectivity. Mobility and ubiquitous connectivity bring the external world into the plant; cloud applications extend the plant into the external world. Both trends accelerate the erosion of plant perimeters. Use of cloud data stores and applications will also impact cyber risk management. Cloud data centres are high-value targets and increase the likelihood of attacks. Data centre intrusions can also open new pathways into plant systems. Just being connected to the cloud will make hackers more aware of plant systems and encourage malicious activity.
Managing cloud application risk will also be more challenging for industrial organisations. Outsourcing applications reduces the ability to mitigate risks according to internal risk perspectives and forces more reliance on contracts and contract managers to ensure alignment of internal and external risk concerns and actions.
Internet of Things devices
There is plenty of hype surrounding the Internet of Things (IoT). But this is not just another futuristic fad. Industrial companies already recognise the potential benefits of IoT in their commercial activities and are developing IIoT strategies that leverage IoT devices in their operations and products.
As IIoT builds upon current and emerging technologies, ARC expects that its adoption will be rapid and widespread. Leading industrial suppliers clearly agree as many have already launched major IIoT programs using catchy terms such as ‘Smarter Planet’ (IBM), ‘Internet of Everything’ (Cisco), and ‘Industrial Internet’ (GE). In Europe, ‘Industrie 4.0’ is also taking hold. All recognise IIoT’s potential for driving significant improvements in asset and operational performance.
The diversity of IIoT opportunities makes it difficult to predict all the ways that organisations will use IoT devices in industrial control systems, but we can be sure that system designers will find creative ways to take advantage of this enhanced intelligence and connectivity. Initial applications will likely involve adding wireless, remotely accessible sensors to plant systems to help improve asset management. As comfort levels grow, use of IIoT will spread across all industrial business processes and connect many external devices with plant systems. These developments will change the very nature of industrial control and the responsibilities of ICS engineers and cybersecurity personnel.
IIoT will be applied within and outside plants, so the urgency for security-by-design devices will rise across the spectrum of industrial controllers, networks and devices. This multi-environment use will also accelerate the shift to wireless, IP-based industrial protocols and demand more use of encryption and device authorisation. As local intelligence expands, managing software updates will become more complex, necessitating more supplier responsibility and involvement in security strategies.
A secure IIoT requires shifts in perspective and focus
To avoid problems, organisations need to be prepared for the changes that will ensue with the IIoT. Industrial adoption of developments like mobility, cloud, and IoT devices will take time, but history tells us that it will probably occur with little input from those responsible for cybersecurity. Lack of advanced planning will therefore place organisations at considerable risk and limit future strategic options.
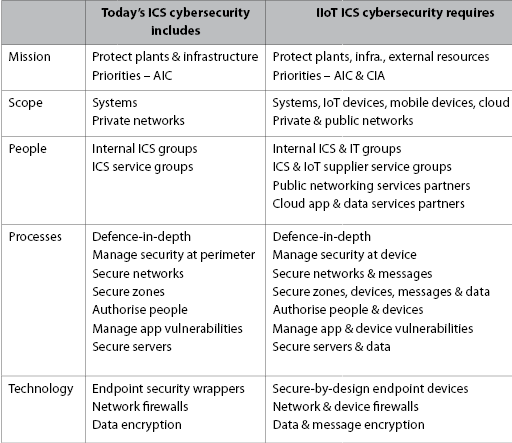
Organisations need to review all aspects of their cybersecurity strategies to understand how these developments impact their current plans. While organisations differ, the table reflects the kinds of changes that should be anticipated. Every organisation should review its strategy in every area from industrial cybersecurity scope to choice of technologies.
Mission and scope
Protecting the availability and integrity of critical assets will remain the central mission of industrial cybersecurity programs, but the scope will broaden to include devices, systems, and services outside traditional plant and scada perimeters as critical assets. Current scopes reflect the reference architectures used in standards like IEC-62443. While these architectures will remain relevant for plants and automation systems (including both in-plant control systems and wider-area scada systems), these facilities will become elements in larger industrial control ecosystems. Embracing this expanded scope will be essential to develop effective plans for the new challenges that will develop.
Some organisations will want to maintain their current ICS cybersecurity scope, but smart companies already recognise the inherent weakness of this position. The devastating impact of peripheral attacks on industrial IT systems, like Shamoon, shows that performance of industrial companies already depends upon the availability of complete, end-to-end industrial business processes. Moreover, this dependence will grow as industry continues to strive for better performance and lower costs. Many plants are already optimised and, increasingly, industrial organisations are looking for opportunities in tighter integration of plants, customers, partners and logistics services. Many are also increasing use of external services to reduce costs and help overcome the challenges presented by an ageing workforce.
People
Today, most companies view ICS cybersecurity as an internally focused, ICS issue. While it is common to use ICS suppliers and third parties for assessments, audits and training; the day-to-day incidents are generally addressed in-house. Accordingly, increasing the cyber-security expertise of engineering staffs has become the focus of organisational strategies.
While understandable, many organisations already recognise the limitations of this approach. Backlogs of software revisions and patches are growing, cybersecurity technology complexity is increasing, and the shortage of ICS cybersecurity expertise forces them to rely more on their ICS suppliers and third parties. The coming developments will certainly exacerbate this situation and require even more outside support. As scope expands, this will lead to the expectation that all suppliers of critical devices, systems and services will have to assume primary responsibility for the ongoing security of their products.
Processes
Process recommendations in current ICS cybersecurity standards are well designed and proven through years of use. Concepts like defence-in-depth will certainly be as relevant in the future as they are today, but other assumptions will have to be reviewed and adapted for the broader scope of protection required for the Industrial Internet of Things.
The ability to protect critical assets with secure perimeters, zones and conduits will certainly become challenging when many of these assets are located in open environments and accessed through a variety of public networks. To accommodate these changes, processes will have to place more emphasis on secure devices and secure message protocols. This will likewise necessitate change in user-centric authorisation processes to include additional factors like device authorisation and location. Risk analysis is another process that will have to broaden and include threats to external devices, systems and services.
Future ICS cybersecurity strategies will also require adding some new processes e.g. to remotely manage device credentials, patches and new applications. Physical device security will also become an issue to protect against theft of credentials and network login information. Fortunately, these are not new issues to the overall cybersecurity community and ICS teams should be able to leverage the lessons learned by groups that manage mobile and cloud security.
Technology
Like processes, ICS cybersecurity technology is already quite mature. Most organisations believe that they have enough to handle most of today’s risks. Ensuring that individual endpoint devices incorporate these capabilities will be the primary challenge for the IIoT.
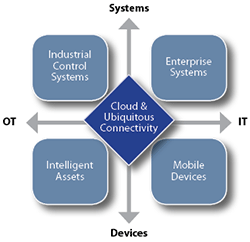
An IIoT view of the cybersecurity challenge
Explosive growth in smart devices like the Nest thermostat prompted considerable interest in IT that controls the physical world. Operational technology (OT) emerged as a new term for distinguishing these applications from those used on information technology (IT) devices like tablets and smartphones, which focus on collecting and managing information.
This IT-OT dichotomy has been a useful tool in understanding the core issues that separate ICS and IT cybersecurity. It provides a convenient way to classify the purpose of individual cyber assets and evaluate the need for special constraints on external accessibility, reboots, patch testing, etc. Aligning these needs with existing cyber capabilities will help organisations establish responsibility boundaries and identify areas requiring additional resources and training.
While powerful, IT-OT analysis is not rich enough to address all IIoT cybersecurity issues. Tomorrow’s industrial cybersecurity programs will have to ensure that the organisation’s internal and external systems and devices are fully protected and that all third-party services are secured against attacks that might leak into critical systems. The figure illustrates this more complicated cybersecurity environment and the different kinds of cybersecurity strategies that will be required.
Security requirements and constraints vary across the different kinds of technologies involved in the IIoT. As discussed above, industrial control and enterprise systems will continue to have different IT-OT goals and constraints that require different practices and skills. IT organisations already recognise that mobile device cybersecurity is different and requires special practices to manage confidentiality and privacy of local data and apps. Intelligent assets have similar needs, but differ in their IT-OT responsibilities and constraints. Managing the cybersecurity of third-party systems and devices will require yet another set of practices, since they are shared, and managed by third parties with different views regarding cyber risks and management strategies.
Guidelines, standards, and best practices are already available for most individual cybersecurity areas. However, the various approaches have a lot of overlap. Like the current deliberations regarding ICS and IT cybersecurity, these overlaps will need to be addressed to eliminate confusion and inefficiency. Smart organisations will recognise this broader landscape in current discussions and develop a single, coherent, future-proof, integrated Industrial Internet of Things cybersecurity strategy.

About the Author
Sid Snitkin, a senior member of ARC Advisory Group’s management team, currently leads ARC’s research into and consulting practice for ICS cybersecurity and related areas. Sid has over 35 years of experience in automation, information systems and manufacturing. He has been with ARC since 1997 and has published numerous studies and strategic reports on a broad range of topics.
For more information contact Paul Miller, ARC Advisory Group, +1 781 471 1141, [email protected], www.arcweb.com
© Technews Publishing (Pty) Ltd | All Rights Reserved