
Is your ICS IT-security more effective than that of Nato or of nuclear energy plants? If not, best you read on.
In mid-2010 the Iranian nuclear industry suffered a major setback as a result of the Stuxnet computer malware – the first known malware targeted at Industrial Control Systems (ICS).
In mid-2014, Dragonfly, a second piece of malware targeted at ICS systems was discovered in the wild. Following hot on the heels of that discovery, in early October 2014, ICS-CERT alerted the ICS fraternity to the presence of the BlackEnergy2 virus1 and towards the end of 2014, the German Federal Office for Information Technology reported on physical damage at a blast furnace site after its ICS was compromised by a malware attack.2
Dragonfly
The name Dragonfly is used by Symantec to refer to the 'Dragonfly hacking group'. It has now become synonymous with a campaign, attributed to that group, aimed at stealing intellectual property from, inter alia, governments, utilities and the energy and manufacturing sectors. Dragonfly has been shown capable of discovering and listing OPC servers and OPC tags across ICS. That information could subsequently be used for industrial sabotage.
Aliases / associated with / in the same family as: Havex, Energetic Bear, Backdoor.Oldrea, Trojan.Karagany, Fertger, Peacepipe, Crouching Yeti.
Timeline
2014-05-12 The National Cyber Awareness System publishes confidential information3 on malware that it calls Dragonfly, which, “. . . allows remote attackers to execute arbitrary commands via unspecified vectors.”
2014-06-23 Finnish security company, F-Secure, publishes a report titled “Havex Hunts for ICS/SCADA Systems”.4 According to this report, F-Secure has been monitoring the Havex malware family and the group behind it for the prior year. In early 2014, the malware targeted industrial control systems through compromised downloads from multiple legitimate ICS suppliers. Of particular interest from this report:
• One of the components of the malware is able to harvest information from compromised systems.
• The malware leverages security flaws in OPC classic (previously OLE for Process Control) and the underlying Microsoft DCOM technology on which OPC classic was built, to gain information about connected devices, and to relay that information to Command and Control (C2) servers.
• F-Secure has recorded 88 variants of the malware.
2014-06-30 Symantec Security Response releases a whitepaper5 detailing a campaign that it refers to as, “[A]n ongoing cyber espionage campaign dubbed Dragonfly (aka Energetic Bear)”. Symantec started monitoring the Dragonfly group in 2012. According to that whitepaper, initial targets were defence and aviation companies in the US and Canada, and then in spring 2013 the focus shifted to US and European energy firms. The Symantec whitepaper notes:
• The Dragonfly operation shows signs of being state-sponsored.
• File dates and times seem to indicate regular daily working hours which tie in with the Eastern European time zone (UTC +2).
• Dragonfly utilises three methods to compromise systems – phishing emails, watering hole attacks and trojanised software upgrades.
• Oldrea gathers system information, file and program lists, Outlook address book data and VPN configuration files. This data is then written to a temporary file in an encrypted format before being sent to a remote C2 server controlled by the attackers.
• Karagany can upload stolen data, download new files, and run executable files on an infected computer. It is also capable of running additional plug-ins for password collection, screen capture and cataloguing documents.
2014-07-01 ICS-CERT issues Advisory ICSA-14-178-01 as a follow-up to updated alert CS-ALERT-14-176-02A. The follow-up provides additional details on Havex and ISC. Key aspects of this alert:
• The known components of the identified Havex payload do not appear to target devices using the OPC Unified Architecture (UA) standard.
• The Havex payload has the capability of enumerating OPC tags.
• ICS-CERT has not found any additional functionality to control or make changes to the connected hardware.
• The Havex payload has caused multiple common OPC platforms to intermittently crash. This could cause a denial of service effect on applications reliant on OPC communications.
2014-07-17 FireEye releases a detailed report6 after examining the OPC activity of one variant of Havex. According to the report:
• The malware scans for OPC servers on the infected machine and laterally across the network, building a list of all OPC servers that are globally accessible through Windows networking, along with the capabilities supported by each such server discovered.
• The details of discovered servers and of their capabilities are saved in two separate unencrypted .dat files, and once the recursive scanning task is completed, the unencrypted log is encrypted using a 168-bit 3DES key.
• The version of Havex used in this test also creates a file for each OPC server, with its state and with each OPC tag enumerated by tag name, tag type, access level and id.
• It is presumed that encrypted files are sent to one of the many C2 servers under the control of Dragonfly.
2014-07-31 A report7 by the Global Research and Analysis Team (GReAT) team at Kaspersky Labs is published with a few new takeaways:
• Globally they have observed about 2800 victims of Dragonfly.
• Most victims are in the industrial / machinery building sector.
• It appears that the campaign originated at the end of 2010.
2014-09-15 Belden announces the outcome of a study8, which it commissioned Joel Langill of RedHat Cyber to undertake, in order to discover more about Dragonfly. This study reveals:
• The three targets of the trojanised software are primarily suppliers to the pharmaceutical sector, not the energy sector.
• Dragonfly bears some resemblance to the Epic Turla attack, which [according to Langill] targeted the IP of pharmaceutical companies.
• The Industrial Protocol Scanner of Dragonfly searches for devices on TCP ports 44818 (Omron, Rockwell Automation), 102 (Siemens) and 502 (Schneider Electric). These protocols and products have a higher installed base in packaging and manufacturing applications typically found in consumer packaged goods industries, such as pharmaceutical rather than the energy industry.
• [Consequently] the [current] target is most likely the pharmaceutical sector, not the energy sector.
2015-02-12 Fast-forwarding to 2015, there is no doubt more to be revealed about Dragonfly and its successful exploits in ICS.
BlackEnergy2
The BlackEnergy toolkit is malware used for criminal purposes and first saw the light of day in 2007. Originally crafted for the creation of botnets for use in DDoS, it has evolved in several different directions and is today used for spamming, theft of bank credentials, password theft, state-on-state cyber-terrorism, and in one of its latest guises, for industrial espionage through scada systems.
Because the toolkit is widely available and used by many different groups for different purposes, it is not easy to attribute its usage in the ICS space to a particular group. Its application in theft of IP via scada systems was first reported in August 2014.
Aka / associated with / in the same family as: Sandworm, BKDR_BLACKEN.A and BKDR_BLACKEN.B, Blakken, Fonten
Timeline
2014-10-08 ICS_CERT releases a TLP Amber alert (ICS-ALERT-14-281-01P) to its US-CERT secure portal.
2014-10-14 iSIGHT Partners, which has been analysing Sandworm (BlackEnergy2) and working closely with Microsoft, reports9 on the discovery of a zero-day vulnerability affecting all supported versions of Microsoft Windows, Windows Server 2008 and 2012, and Microsoft releases a patch for this vulnerability (CVE-2014-4114). Key aspects of the iSIGHT report:
• The campaign’s purpose is cyber espionage.
• The campaign is attributed to the Sandworm team.
• The campaign is tightly targeted, with victims being Nato, Ukrainian government organisations, a Western European government organisation, energy sector firms (specifically in Poland), European telecommunications firms and a US academic organisation.
• Although the Sandworm team had been targeting Nato and others before this latest assault, attacks using this zero-day vulnerability started in June 2014.
2014-10-16 Trend Micro’s TrendLabs reports new findings10, the most important of which is that one of the attack vectors is via GE Intelligent Platform’s CIMPLICITY HMI solution suite.
2014-10-21 iSIGHT Partners reports11 additional information related to the scada attack vector, noting that additional files suggest that Siemens WinCC scada is also being used as an attack vector.
2014-10-29 ICS-CERT publishes an alert12 concerning an ongoing malware campaign using a variant of the BlackEnergy malware. Key points from the report:
• The campaign has compromised numerous ICS.
• The campaign has been ongoing since at least 2011.
• Multiple companies have identified the malware on Internet-connected HMIs from the product families GE Cimplicity, Advantech/Broadwin WebAccess and Siemens WinCC.
• Any companies that have been running Cimplicity since 2012 with their HMI directly connected to the Internet could be infected.
2014-11-03 Kaspersky labs’ Securelist publishes a detailed report13 on BlackEnergy2. From a control and instrumentation perspective, the key takeaway of the report is that a set of victims discovered that Siemens’ “ccprojectmgr.exe” [WinCC] was responsible for downloading and executing BlackEnergy between March 2014 and July 2014.
2014-11-21 Siemens publishes an Industrial Security Alert recommending users to update SIMATIC WinCC to the latest release [which addresses the ICS-CERT alert]. The company also issues a detailed Security Advisory SSA-134508: Vulnerabilities in SIMATIC WinCC, PCS 7 and WinCC in TIA Portal.14
2015-02-12 As the year progresses we expect there will be further revelations of this group targeting owners of scada systems – either to extract information about those systems or as a backdoor into their corporate systems for espionage and worse.
German blast furnace incident
In mid-December 2014 the German Federal Office for Information Technology (BSI) published its report2 on the state of IT security in 2014, in which it describes a targeted attack on a German steel plant. The malware entered the company’s office network via sophisticated phishing and social engineering vectors and from there gained access to the production network. The plant experienced an increased frequency of individual components and of production units. Ultimately this led to a situation in which the control system was unable to bring the blast furnace to a safe state and massive damage occurred.
Unfortunately, BSI has so far revealed very little about the incident. However, at least one industry commentator has suggested that it can probably be attributed to either Dragonfly or BlackEnergy.15
Points to ponder
Are we to take these attacks at face value and assume they are purely industrial espionage, or are they the first phase of a search and destroy mission in which the stolen information on control system topologies and OPC tags is used to cause not only economic hardship for targets through loss of IP, but also loss of production capacity and injury to personnel through subsequent sabotage?
We subtitled this article, “Complacency could kill careers, co-workers and companies”, so let’s wrap it up by turning our backs on technicalities and facing some of the consequences of failing to adequately secure an IT installation.
Career killer
After the Sony hack, which revealed to the world at large, amongst other items, the content of 5000 of her private emails, Amy Pascal was fired as co-chair of Sony’s movie studios. It would not stretch the bounds of belief to imagine that one or more senior IT members also found themselves looking for a new career.
Co-worker killer
The German blast furnace incident must be a huge wake-up call to all IT practitioners who oversee C&I networks. Five thousand cubic metres of charge at around 1500°C is an immense amount of energy to lose control of. In November 2013, a blast furnace being commissioned at Bhushan Steel in India exploded killing at least one worker and injuring many more. As a result of the incident, three top officials of BSL, including its chief operating officer (COO), were arrested on charges of negligence.
Company killer
On its own, cyber espionage can destroy a company. Key intellectual property that is stolen can leave industry-leading companies with no unique selling proposition once their IP such as developments, detailed designs, engineering drawings, recipes, process steps, operating parameters, customer list and source code etc. are revealed to unscrupulous competitors. All it takes is one incident and a company can be forced into bankruptcy and closure.
On 17 June 2014, Code Spaces, a site that provided code hosting services which were ultimately hosted on Amazon’s Elastic Compute Cloud, was subjected to a DDoS. Reportedly the attacker demanded a significant ransom. The company failed to agree to the ransom and attempted to lock the intruder out, to which his response was to wipe all the company’s files on Amazon’s Cloud infrastructure. According to a statement published at the time on its website, “We finally managed to get our panel access back but not before he had removed all EBS [Amazon Elastic Block Store] snapshots, S3 [Amazon Simple Storage Service] buckets, all AMI’s [Amazon Machine Images], some EBS instances and several machine instances. In summary, most of our data, backups, machine configurations and offsite backups were either partially or completely deleted.”
Immediately after this devastating attack, the company announced, “Code Spaces will not be able to operate beyond this point, the cost of resolving this issue to date and the expected cost of refunding customers who have been left without the service they paid for will put Code Spaces in an irreversible position both financially and in terms of ongoing credibility.”
Takeaways
1. Antivirus systems typically respond to known attack vectors, not zero-day exploits. Campaigns like Stuxnet, Dragonfly and BlackEnergy2 were active for typically two years or more before being exposed. Based on past performance, this means that your ICS infrastructure may already be compromised by 2016’s, 2017’s or 2018’s killer APT.
2. Just because there are no obvious signs of malware in your ICS (computers that fail to boot, high traffic volumes, etc.), it does not mean that your system is not already controllable by an outsider group.
3. No company or organisation is too big or too small to avoid being a potential targeted victim of a malware campaign that steals intellectual property and / or sabotages plants and processes.
4. If your scada system becomes the target, or worse still, the victim, of one of these campaigns your job security and career path will be affected.
5. If your plant becomes victim to malware and consequent sabotage, as in the German case quoted above, senior management of all designations and certainly of the IT and engineering divisions could face arrest, compensation claims and possibly years behind bars.
6. If you are living in the misguided belief that your cloud-based service provider is protecting your data and backups, you have work to do.
7. Your company may not survive the destruction of all of its software, data assets and backups.
8. Don’t write emails with the premise that they are confidential. If each and every one of them was published in the public domain, would their contents cause you embarrassment?
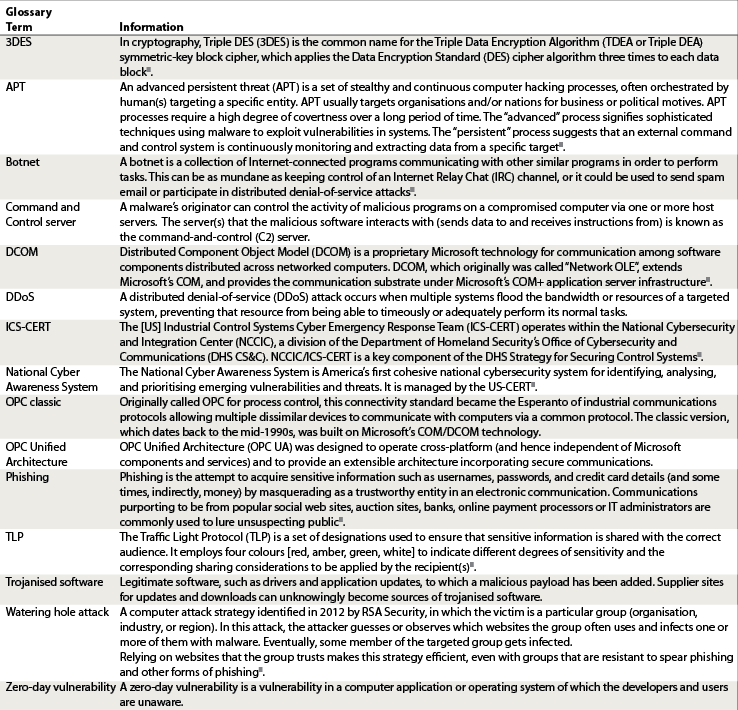
Glossary references
1. Wikipedia, http://en.wikipedia.org/, [2015-02-12].
2. ICS-CERT, https://ics-cert.us-cert.gov/, [2015-02-12].
3. US_CERT, Frequently Asked Questions, https://www.us-cert.gov/faq, [2015-02-12].
4. US-CERT, Traffic Light Protocol (TLP) Matrix and Frequently Asked Questions, https://www.us-cert.gov/tlp, [2015-02-12].
Article references
1. ICS-CERT, Alert (ICS-ALERT-14-281-01B) Ongoing Sophisticated Malware Campaign Compromising ICS, 2014-12-10, http://tinyurl.com/ldzw6m6, [2015-02-12].
2. Bundesamt für Sicherheit in der Informationstechnik, Die Lage der IT-Sicherheit in Deutschland 2014, 2014-12, http://tinyurl.com/ns4sy2g, [2015-02-12].
3. National Vulnerability Database, Vulnerability Summary for CVE-2013-5671, 2014-05-12, http://tinyurl.com/jwzuxt2, [2015-02-12].
4. F-Secure, Havex Hunts for ICS/SCADA Systems, 2014-06-23, http://tinyurl.com/p65plco, [2015-02-12].
5. Symantec Security Response, Dragonfly: Cyberespionage Attacks Against Energy Suppliers, 2014-07-07, http://tinyurl.com/kauk4q4, [2015-02-12].
6. FireEye, Havex, It’s Down With OPC, 2014-07-17, http://tinyurl.com/ogxd3ty, [2015-02-12].
7. Kaspersky Lab, Energetic Bear: more like a Crouching Yeti, 2014-07-31, http://tinyurl.com/pnmjj9y, [2015-02-12].
8. BusinessWire, Belden Research Reveals Dragonfly Malware Likely Targets Pharmaceutical Companies, 2014-09-15, http://tinyurl.com/pbljj9e, [2015-02-12].
9. iSIGHT Partners, iSIGHT discovers zero-day vulnerability CVE-2014-4114 used in Russian cyber-espionage campaign, 2014-10-14, http://tinyurl.com/mzsjsjk, [2015-02-12].
10. Trend Micro, Sandworm to Blacken: The SCADA Connection, 2014-10-16, http://tinyurl.com/oy5oan3, [2015-02-12].
11. iSIGHT Partners, Sandworm Team – Targeting SCADA Systems, 2014-10-21, http://tinyurl.com/m4b7at3, [2015-02-12].
12. ICS-CERT, Alert (ICS-ALERT-14-281-01B) Ongoing Sophisticated Malware Campaign Compromising ICS (Update B), 2014-12-10, http://tinyurl.com/ldzw6m6, [2015-02-12].
13. Kaspersky Lab, BE2 custom plugins, router abuse, and target profiles - New observations on BlackEnergy2 APT, 2014-11-03, http://tinyurl.com/nf8t3ok, [2015-02-12].
14. Siemens, SSA-134508: Vulnerabilities in SIMATIC WinCC, PCS 7 and WinCC in TIA Portal, 2014-11-21, http://tinyurl.com/o2j9fmb, [2015-02-12].
15. ICS-SANS, ICS CP/PE (Cyber-to-Physical or Process Effects) case study paper – German Steel Mill Cyber Attack, 2014-12-30, http://tinyurl.com/k9lwbpw, [2015-02-12].

About the author
Andrew Ashton has electrical, mechanical and business qualifications and has been active in automation and process control since the early 1980s. Since 1991 he has headed up a company that has developed formulation management systems for the food, pharmaceutical and chemical manufacturing industries and manufacturing solutions involving the integration of various communication technologies and databases. Developed systems address issues around traceability, systems integration, manufacturing efficiency and effectiveness. Andrew is a contributing editor for SA Instrumentation and Control.
| Tel: | +27 31 764 0593 |
| Email: | [email protected] |
| www: | www.technews.co.za |
| Articles: | More information and articles about Technews Publishing (SA Instrumentation & Control) |
© Technews Publishing (Pty) Ltd | All Rights Reserved